Azure Active Directory (Azure AD) Conditional Access is a powerful feature that allows administrators to control access to cloud applications based on specific conditions.
These conditions can include factors such as location, device type, and network status. By using Conditional Access, administrators can ensure that only authorized users are able to access sensitive resources, and that these users are doing so from a secure location or device.
This helps to protect the organization from potential security threats, such as cyber attacks or data breaches. Conditional Access can be configured for specific users, groups, or entire organizations, and can be applied to all cloud applications or specific ones.
Conditional Access can be created and applied to a wide range of applications, including built-in Microsoft applications and any Azure AD integrated applications including gallery, non-gallery, and applications published through Application Proxy.
However, it is important to note that the list provided in the Microsoft website is not exhaustive and there may be certain first party apps that cannot be excluded from the Conditional Access policy. One such example is the Microsoft App Access panel.
There has been a feature request that has appeared in multiple forums, feedback, and other social networking sites which is to exclude the app “Microsoft App Access panel” from the conditional access policy.
This feature request is driven by various use cases such as B2B collaboration and setting up MFA from untrusted devices, etc. For more information about this feature request and related discussions, please refer to some of the posts in forums and feedback sites.
https://feedback.azure.com/d365community/idea/d5253b08-d076-ed11-a81b-000d3adb7ffd
Support conditional access for MyApps.microsoft.com · Community (azure.com)
A new preview feature from Microsoft for 'my apps' now allows for exclusion in conditional access policies.
If this option is set to yes, applications will be launched from the new My Apps launching endpoint improving performance and resilience as well as addressing existing issues with conditional access for My Apps. If this option is set to no, applications will continue to be launched from the legacy https://account.activedirectory.windowsazure.com endpoint
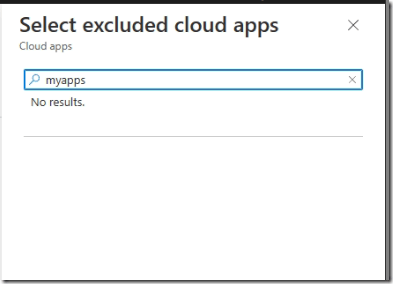
Before we enable the preview feature, if you search for myapps in conditional access policy (excluded cloud apps), you will not find it.
How to enable the My apps for conditional access policy?
Go to Azure AD portal, click on enterprise applications https://entra.microsoft.com/#view/Microsoft_AAD_IAM/StartboardApplicationsMenuBlade/~/AppAppsPreview
Under manage, you will see app launchers, click on it
Click on settings https://entra.microsoft.com/#view/Microsoft_AAD_IAM/AppLaunchersBlade/~/Settings
you will see preview settings, enable the settings and save it.
Now lets create a new conditional access policy or use existing conditional access policy to exclude Myapps application
After you create or update the conditional access policy, user can go to https://myapps.microsoft.com, Click “Try the preview”, then you could click the application you want to access.
Current View:
Preview view:
This preview feature should help to explore higher possibilities to improve the end-user experience with conditional access policies.