Role-based access control (RBAC) helps you manage who has access to your organization’s resources and what they can do with those resources. By assigning roles to your Intune users, you can limit what they can see and change. Each role has a set of permissions that determine what users with that role can access and change within your organization.
To create, edit, or assign roles, your account must have one of the following permissions in Azure AD:
- Global Administrator
- Intune Service Administrator (also known as Intune Administrator)
we are into MAM ONLY and no device enrollment. When a device is lost or stolen, or if the employee leaves your company, you want to make sure company app data is removed from the device. But you might not want to remove personal data on the device, especially if the device is an employee-owned device.
To perform selective wipe, the user who perform the action must have enough intune permissions. It is not possible to give intune admin role instead, we ca make use of RBAC to create require permissions to perform selective wipe only.
Following are the RBAC permissions needed to perform selective wipe task.
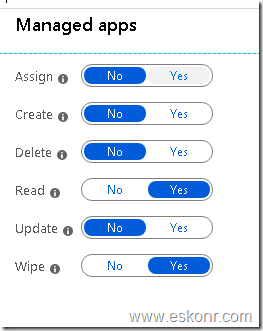
add Custom role with following permissions.
Managed apps: select Read ,wipe to Yes
Managed devices: Select read to Yes
Mobile App: Select Read to Yes
Once you create the RBAC role, assign it to AD sec group with scope target to group . To know more about scope tags in intune ,read https://docs.microsoft.com/en-us/intune/scope-tags
How to wipe only corporate data from Intune-managed apps https://docs.microsoft.com/en-us/intune/apps-selective-wipe
Reference: